Migrating to AWS? Time to start thinking about AWS security best practices. Securing your new AWS infrastructure not only falls on the IaaS provider, but on your organization as well. To avoid risk in the cloud, keep in mind some AWS security best practices before you make the move. The below list is not exhaustive but meant to get you started.
Know the Shared Responsibility Model
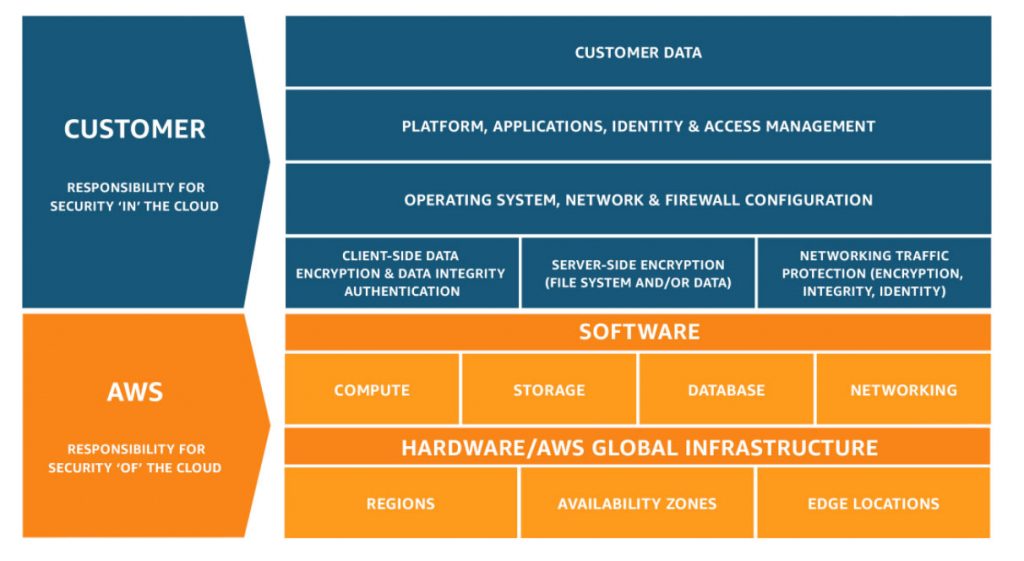
AWS uses a shared responsibility model, which means that both Amazon and your organization are responsible for maintaining security in your infrastructure. AWS is responsible for securing the lower layers of the stack, meaning they make sure the infrastructure as a whole is secure, while the organization is accountable for everything else up to and the application layer, essentially your instance.
AWS Customers are responsible for:
- Customer data
- Platform, applications, identity, and access management
- Operating system, network, and firewall configuration
- Client-side data encryption and data integrity authentication
- Server side encryption
- Network traffic protection
Extend Your Security Model
Many of the security and compliance concepts you already have in place apply in the cloud. Minimize the time and resources needed to secure your new cloud instance by leveraging the tools, processes, and practices you already have developed as a starting point.
Follow Identity and Access Management (IAM) Best Practices
IAM provides user provisioning and access control capabilities for AWS users. IAM policies should be attached to groups or roles rather than individual users to minimize risk of a user getting excessive permissions by accident. IAM users should have multifactor authentication activated and be given minimal access privileges (least privilege access) to AWS resources but still be able to fulfill their job responsibilities.
Audit
You need oversight into user activities and to make sure you are tracking them to identify possible account compromises, insider threats, and hijacking. AWS CloudTrail provides event history of your AWS account activity and should be used to audit your infrastructure.
Security Patching
It is the customer’s responsibility to make sure that the latest security patches have been applied to an environment. Make sure you are regularly applying security patches released by vendors. Even if the systems aren’t publicly accessible, still patch your servers. Threats can come from inside your network just as easily as outside
Network Security
Using firewalls and network access control lists prevent the wrong kind of traffic from getting to your servers. As a rule of thumb, only the network traffic that is essential should be allowed, and all other network traffic should be blocked. Further, servers with sensitive data should be protected via a DMZ from Internet traffic.
Use Encryption
Enable encryption within your AWS infrastructure to protect any sensitive data, which provides protection with only minimal overhead. You could also implement scalable key management to create, rotate, define, and audit your encryption keys in one place. Data should both be protected in transit and at rest.
Your organization should also use both server and client-side encryption. AWS provides client-side encryption with S3, EBS, and RDS.
Backup Your Data
This may seem elementary but in the event that something should happen, making sure that your data is backed up could mean the difference between staying in business and going out of business. Your unique backup strategy depends on your current setup and industry requirements, but AWS offers flexible backup and restore solutions for everyone. AWS has automated, tiered solutions to data archival designed to fit most any need.
These AWS security best practices just scratch the surface of everything to keep in mind when you are developing security policies and procedures for your new AWS cloud infrastructure. Need help integrating security into your migration plan? Contact WSM today.